Much has been written about how COVID-19 has impacted cybersecurity during 2020, from heightened cybersecurity threats to foundationally challenging business resiliency. However, there are other lessons for cybersecurity which are unnoticed or under-emphasized. Swiss...
Your phone’s status bar is tracking you
As of today, any application on the Apple iOS mobile platform can determine your location and uniquely fingerprint your mobile activity without any indication or user authorization. Even the most innocent-looking applications can gather personal information in this manner.
Researchers at Level Nine have discovered multiple lapses in platform security that allow malicious applications, an attacker, or advertisers to use this information against you. Many of these techniques are known by small communities of developers who sell user tracking software to advertisers or state sponsored hacker groups.
How is this possible?
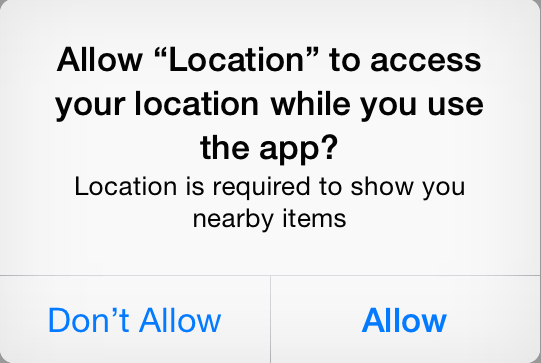
This technique is performed by collecting cellular signal strength, Wi-Fi signal strength, and magnetometer readings of a user’s surroundings. This article revolves around the ability to obtain both cellular and Wi-Fi signal information, a future post will outline the danger of unauthorized magnetometer access. While GPS coordinates provide an accurate location of a user, the use of GPS by any mobile application requires explicit user approval and could alert the user to the application’s malicious intentions. The technique described here, requires no user interaction and can be performed even if the user explicitly declines that location information be provided to the application.
The Status Bar
Ever notice that bar displayed on every application screen? It displays your battery strength, time of day and other phone status information.
While icons themselves provide insight into how the user has configured the device, a much deeper, more invasive, amount of information lies in the values that drive these icons. Any in-use application can access these values and use them to approximate the user’s physical location.
The following is a subset of privacy invasive data points that can obtained about a user through this technique.
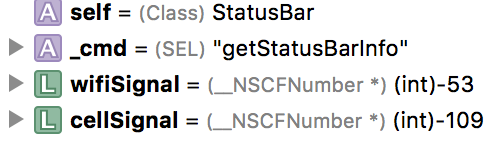
Cellular signal strength (those 5 dots)
- The dots you see are actually powered by a much more precise number between -40 and -120. This is referred to as the “RSSI” or Received Signal Strength Indication and corresponds to the exact distance from nearest cellular tower and/or interference. The cellular signal strength can be used to pinpoint the cellular area the user is currently in; the area may be unknown, but it is unique.
WiFi signal strength
- Similar to cellular strength, this numerical value is an excellent form of near-field tracking when combined with cellular signal strength. A device can be reliably tracked as it moves within a given WiFi range. When combined with cellular strength, a very precise measurement can’t be taken. For Example, moving from the front yard, to inside, upstairs, or even another room in your house will greatly impact the WiFi signal.
It is highly likely that many applications already exist that make use of this privacy leak. The manner in which it can be achieved is not aggressive in nature and can often be masqueraded to bypass application store checks.
What’s the problem?
Applications can use this information to detect your location/movement or create unique identifiers for your device. There are two implications to a device owner when this information is unintentionally made accessible to mobile applications.
Location Tracking
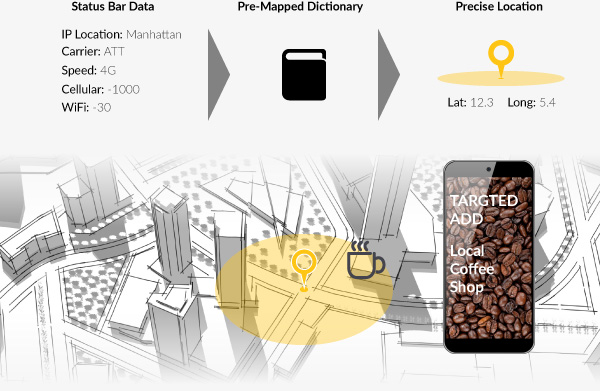
This information can be used to accurately fingerprint a person/device and identify their location. Marketers or attackers can the device’s high-level geo location from it’s IP address and further collection the Wi-Fi signal strength, cellular signal strength, and carrier name/speed from the status bar. This information can then be mapped to real GPS coordinates to create a dictionary.
This can be done by taking various carrier devices to an establishment, “fingerprinting” it’s cellular, and Wi-Fi readings while recording the current GPS signal. For example, a marketer could map out the different cellular signal strengths for ATT, Verizon, T-mobile, etc in different parts of a city by walking down the streets and recoding the levels along with various free Wi-Fi access points and their associated strengths. This data could then be coupled with IP Geo location to ensure the same general location.
Once this database is created, it can be referenced by attackers or advertisers who extract this data from your device’s status bar. The result is real GPS coordinates of your location without any authorization or indication. This is all possible without ever using the device’s GPS sensor. In populated areas, this information could be used to serve extremely targeted ads for nearby businesses that the user may be near.
Techniques to obtain this information are not well known, despite the fact that Apple’s iOS SDK code contains headers that identify the fields. The ED research team was able to reliably test this technique and extract proper signal information from any device, starting with iOS 4 through the latest iOS 10.2 build.