Much has been written about how COVID-19 has impacted cybersecurity during 2020, from heightened cybersecurity threats to foundationally challenging business resiliency. However, there are other lessons for cybersecurity which are unnoticed or under-emphasized. Swiss...
Threats and Solutions to Wide Body Area Networks

The healthcare industry is under continuous attack with cybercriminals targeting poorly controlled medical devices (Schiano, Sharman, and McClean, 2018). In the first two months of 2018, 24 healthcare organizations reported data breaches affecting over 1,00 patients each (Schiano, Sharman, and McClean, 2018). Healthcare networks are historically designed without segmentation; thus, giving attackers easy lateral access one inside (Schiano, Sherman, and McClean, 2018). These types of attacks will continue to increase as more healthcare organizations report the data breaches.
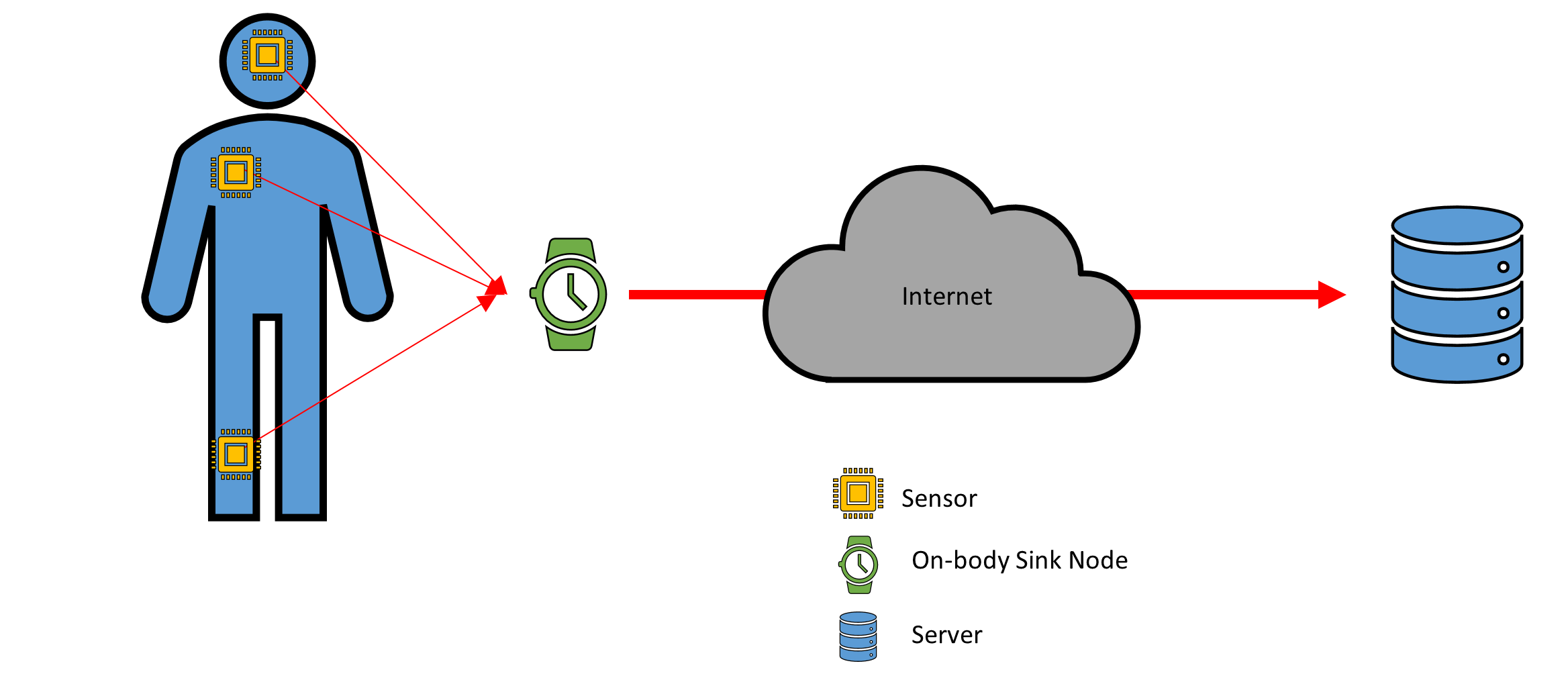
The medical device threat landscape continues to grow as they are placed inside of human beings. Performance advances in processors and wireless communication as allowed for the creation of Wireless Body Area Network (WBAN) (Ali, Ghani, Khan, Chaudhry, Islam, and Giri. 2020). In WBAN, there are sensors placed throughout the body that monitor different health aspects (Ali et al., 2020). The sensors authenticate to an on-body sink node (Ali et al., 2020). The on-body sink node then authenticates over the internet to the healthcare providers server (Ali et al., 2020).
WBAN architecture raises two threats to be considered; denial of service and tampering (Mucchi, Jayousi, Martinelli, Caputo, and Marcocci, 2020). Denial of service attacks is relevant at the in-body sensor, on-body sink node, and the server. Data tampering is a concern at every stage of the architecture. A sensor tampered within the body can change the information sent to the on-body sink node, or it can be disrupted to where a DoS has caused no data to be sent. There is an added level of criticality because the sensors are implanted. There is concern that a tampered embedded sensor could cause bodily harm to the patient, such as overheating.
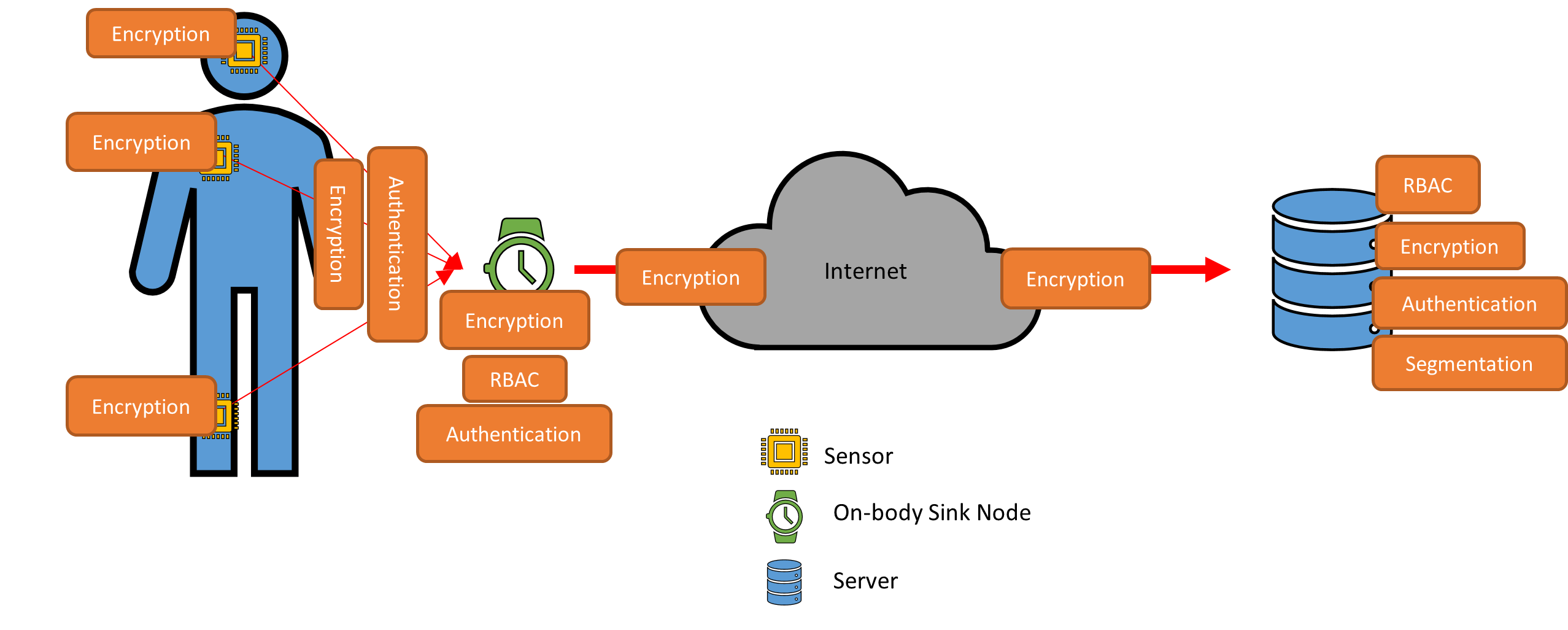
There are security requirements when utilizing WBAN, the main requirements being data authenticity, confidentiality, integrity, availability, access control, and non-repudiation (Mucchi et al., 2020). These security requirements are standard among security professionals. To achieve these requirements, role-based access control (RBAC), authentication, encryption, and segmentation, are the techniques security professionals can use to secure the WBAN environment.
Each implanted sensor will require encryption at rest as well as in motion. Each sensor will be required to authenticate to the on-body sink node. The on-body sink node will communicate on an encrypted medium to the server. The on-body sink node will authenticate to the server. The on-body sink node and the server will have information technology administrators that will be controlled through RBAC to prevent undesirable configuration changes. This security view of the architecture provides some guidelines to securing a WBAN but is not all-inclusive.
As mentioned earlier, the healthcare industry is usually a flat network. The reason this is an issue is because of a hacker’s ability to infiltrate the system and then gain access to other devices through the weaknesses in segmentation design. WBAN raises the criticality of implementing network segmentation because of the implant sensors. A hacker has the potential to gain access to these sensors and cause bodily harm.
To ensure that encryption can be supported, security professionals should evaluate the products that will be providing WBAN services. Encryption protocols will need to meet the needs of the healthcare provider because it is a requirement from HIPAA to protect PHI at rest and in-transit (Vanderpool, 2019). The evaluation of the vendors will provide proof that the product can operate within the standards of the hospital.
Segmentation is achieved in several different ways that will provide defense-in-depth. The WBAN network can be segmented on its own virtual local area network (VLAN). Modern-day switches, no matter the vendor, are capable of utilizing VLANs. There are products to provide granular segmentation, such as Cisco Systems Identity Service Engine (Cisco, 2020). Further segmentation can be done through TrustSec, which is a micro-segmentation platform developed by Cisco Systems (Cisco, 2020).
There is a discovery that must happen on medical devices to be able to have an understanding of their intended communications. To segment, security engineers must be able to understand how medical devices communicate. Once the communication data flow is understood, technical controls can be placed around that data flow to ensure the medical device communicates appropriately but does not allow abnormal network behavior. Some products use artificial intelligence and machine learning, such as Ordr, that provides granular visibility into medical devices (Order, 2020).
In conclusion, the use of WBAN provides healthcare providers with vital information to take a leading edge proactive approach to healthcare. The importance of this emerging discipline will come with security challenges that healthcare provider networks will struggle to meet unless the changes to the infrastructure commence. While the threat landscape will increase, the ability to secure it is still within the means of security professionals to achieve with the help of a few products to target the issue.
References
Ali, Z., Ghani, A., Khan, I., Chaudhry, S. A., Islam, S. H., & Giri, D. (2020). A robust authentication and access control protocol for securing wireless healthcare sensor networks. Journal of Information Security and Applications, 52, 102502. doi:10.1016/j.jisa.2020.102502
Cisco Systems, (2020). Retrieved September 12, 2020 from https://www.cisco.com
Mucchi, L., Jayousi, S., Martinelli, A., Caputo, S., & Marcocci, P. (2019). An Overview of
Security Threats, Solutions and Challenges in WBANs for Healthcare. 2019 13th International Symposium on Medical Information and Communication Technology (ISMICT). doi:10.1109/ismict.2019.8743798
Ordr, (2020). Retrieved September 9, 2020 from https://www.ordr.net
Salvatore, S., Sherman, C., & McClean, C. (2018). Engaging employees in health care data security. Harvard Business Review. Retrieved from: https://www.hbr.org/2018/03/engaging-employees-in-health-care-data-security
Vanderpool, D. (2019) HIPAA compliance: a common sense approach. Innov Clin Neurosci. 2019;16(1-2): 38-41.